Zero Knowledge-rollups unveiled: technical insights into L2, privacy and scalability
Amidst the turmoils of crypto markets and the unstoppable march of blockchain adoption, a quiet revolution is taking root. It’s a transformation driven not by consensus mechanisms alone, but by the subtle power of rollups and the architectural of Layer 2 networks. Enter the age of ZeroKnowledge – where privacy becomes a mathematical certainty and scalability a solved equation.
Article originally prepared in Italian for my personal podcast Disruptive Talks (read it here). This content is also available as a self produced video documentary, here, and in audio podcast, available here.
This trend has captured the attention of both decentralized and centralized titans in the industry, including Ethereum, Polygon, Binance, and Loopring. But what exactly are these Layer 2 and Zero Knowledge technologies? To fully grasp their significance and potential impact, let’s start from the fundamentals and systematically explore each concept.
At the origin of Layer 2 solutions: scalability issues
Since their inceptions, blockchain network have grown and evolved, and they’ve encountered a fundamental challenge that threatens to undermine their potential: the blockchain trilemma.
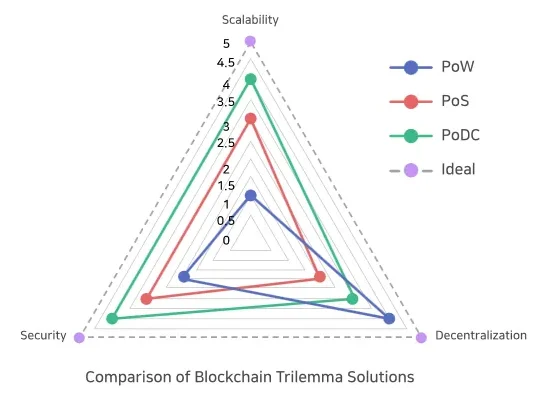
Coined by Ethereum co-founder Vitalik Buterin, the trilemma posits that blockchain systems can only optimize for two out of three critical properties: decentralization, security, and scalability. This trilemma forces blockchain architects and developers to make difficult trade-offs:
- Decentralization ensures that the network is not controlled by a single entity or small group, fostering trust and resistance to censorship.
- Security protects the network from attacks and ensures the integrity of transactions.
- Scalability allows the network to handle a large number of transactions quickly and efficiently.
In practice, most public blockchains have prioritized decentralization and security at the expense of scalability. This choice has led to significant challenges as these networks have grown in popularity and usage.
The issue became glaringly apparent in late 2017 with the CryptoKitties phenomenon on the Ethereum network. CryptoKitties, a game where players could buy, sell, and breed virtual cats, became so popular that it congested the entire Ethereum network. Transaction fees skyrocketed, and the time required to process transactions increased dramatically. At its peak, CryptoKitties accounted for nearly 12% of all transactions on the Ethereum network, causing a sixfold increase in pending transactions.
This event laid bare the limitations of Ethereum’s scalability. The network, capable of processing only about 15 transactions per second, was brought to a near standstill. Regular users found themselves priced out of using the network for everyday transactions, as gas fees (transaction costs) became prohibitively expensive.
The CryptoKitties incident was not just a quirky moment in crypto history; it was a wake-up call for the entire blockchain industry. It highlighted the urgent need for scalable solutions that could handle the growing demand for blockchain-based applications without compromising on security or decentralization.
To understand the scalability challenge, we need to break down three core components of blockchain infrastructure that may be critical for scalability: execution, storage, and consensus.
- Execution: processing and validating transactions
It refers to the processing and validation of transactions. Each transaction must be verified and result in a state change on the network, which can vary in complexity. The challenge here is how to execute a greater number of transactions or computations per second without requiring increasingly powerful hardware for the nodes that validate these transactions.
- Storage: memorization of historical data and global state
It represents the need to maintain an updated copy of the blockchain’s state. Increases in storage requirements for both historical data and the current global state lead to a condition known as ‘state bloat’, making it more difficult for nodes to stay synchronized with the latest state of the network. The central question becomes: how to handle a larger volume of data without overloading the network nodes?
- Consensus: agreement on digital truth
Consensus is the mechanism through which network nodes agree on the validity of transactions, ensuring that the honest majority prevails over potential malicious actors. An efficient consensus mechanism translates into quickly finalized transactions, increasing overall trust and security in the system. However, optimizing this process without compromising security or decentralization presents significant challenges.
To address these points, numerous solutions have been proposed, including multi-chain ecosystems, execution sharding, and payment and state channels. Many of these solutions involve the creation of Layer 2 protocols that operate on top of the main blockchain.
What are Layer 2
Layer 2 solutions operate on top of the main blockchain (Layer 1), offloading much of the computational and storage burden while still leveraging the security and decentralization of the underlying network. Let’s explore the main categories of L2 solutions and their relationship to Zero Knowledge technology.
They enable horizontal scaling of a blockchain by shifting part of the computational load to a parallel chain and reducing the work of the main chain. However, it’s crucial to understand that Layer 2 solutions don’t just process transactions in parallel. They aggregate multiple transactions together before submitting them to the main chain, which is key to achieving scalability. Among the most well-known Layer 2 projects are Lightning Network for Bitcoin and solutions like Optimism and ZK Rollups for Ethereum.
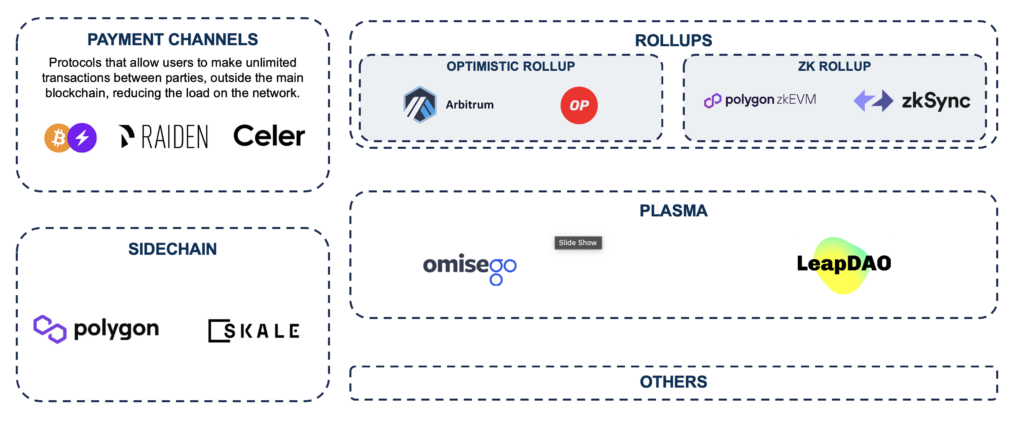
Different types of Layer 2:
- Payment Channels: channels such as Lightning Network for Bitcoin and Raiden for Ethereum, allow users to conduct multiple transactions off-chain, only settling the final balance on the main blockchain. While these solutions significantly reduce the load on the main network, they don’t inherently use Zero Knowledge proofs. However, recent research has explored incorporating ZK proofs into payment channels to enhance privacy and security.
- Rollups: perhaps the most promising L2 solution, especially for smart contract platforms like Ethereum. They come in two main flavors:
- Optimistic rollups: projects like Arbitrum and Optimism use this approach. Optimistic rollups assume transactions are valid by default and only run the computation to verify transactions if they’re challenged. This allows for faster and cheaper transactions, but with a caveat: withdrawals can take up to a week to process due to the challenge period.
- ZK-rollups: this is where Zero Knowledge technology truly shines in the L2 space. ZK-Rollups, exemplified by projects like zkSync and Polygon zkEVM, use ZK-SNARKs or ZK-STARKs to validate the correctness of off-chain computations. This allows for near-instant finality and withdrawals, as the proof of correctness is cryptographically verified on-chain.
The key advantage of ZK-Rollups over Optimistic Rollups is the speed of withdrawals and the cryptographic guarantee of correctness. However, ZK-Rollups are more complex to implement, especially for general-purpose smart contract execution.
- Optimistic rollups: projects like Arbitrum and Optimism use this approach. Optimistic rollups assume transactions are valid by default and only run the computation to verify transactions if they’re challenged. This allows for faster and cheaper transactions, but with a caveat: withdrawals can take up to a week to process due to the challenge period.
- Sidechains: solutions like Polygon’s PoS chain or SKALE, are separate blockchains that run parallel to the main chain and have their own consensus mechanisms. While they offer high scalability, they don’t inherit the full security of the main chain like rollups do. Sidechains can potentially incorporate ZK proofs for cross-chain transfers or to prove the validity of sidechain states to the main chain, enhancing their security model.
- Plasma: framework for creating child chains that periodically commit state roots to the main chain. While projects like OMG Network (formerly OmiseGO) have implemented Plasma chains, the complexity of safe exits in adversarial conditions has limited their adoption. Some Plasma implementations have explored using ZK proofs to compress and verify child chain states more efficiently.
This ecosystem is constantly evolving, with new technologies emerging regularly. However, at present, one of the most promising approaches is the implementation of Zero Knowledge proofs. Let’s delve deeper into this technology and its potential impact on blockchain scalability and privacy.
What is ZeroKnowledge?
The genesis of this tech can be traced to a seminal paper published in 1985 by cryptographers Shafi Goldwasser, Silvio Micali, and Charles Rackoff. Their work, titled “The Knowledge Complexity of Interactive Proof Systems,” introduced a revolutionary idea: the possibility of proving the truth of a statement without revealing any information beyond the validity of the statement itself. This concept, which seemed almost paradoxical at first, would go on to reshape our understanding of privacy in computational systems.
The development of Zero Knowledge proofs was not merely an academic exercise. It was born out of a pressing need in computer science and cryptography to solve complex problems of authentication and verification without compromising sensitive information. In an era where digital communication was becoming increasingly prevalent, the ability to prove knowledge without revealing it held immense potential.
The true power of zk solutions lies in their versatility. At its core, a Zero Knowledge proof allows a ‘prover’ to convince a ‘verifier’ of the truth of a statement without conveying any additional information. This property, known as ‘zero-knowledge’, ensures that the verifier learns nothing except the validity of the assertion. Simultaneously, the proof must be ‘complete’ (if the statement is true, an honest verifier will be convinced) and ‘sound’ (if the statement is false, no cheating prover can convince the verifier that it is true, except with negligible probability). We’ll see later how that applies technically to blockchain solutions.
Today, it is used in blockchains primarily in two ways:
- To create private transactions, where details are visible only to users and not to the network.
- To scale transactions on Layer 2. In this context, we refer to Zero Knowledge Succinct Non-interactive Arguments of Knowledge (ZK-SNARKs).
But, concretely, how does it work? Let’s examine a non-exhaustive illustration of Zero Knowledge technology applied to blockchain. Keep in mind that every solution involves different layers and may vary in implementation.
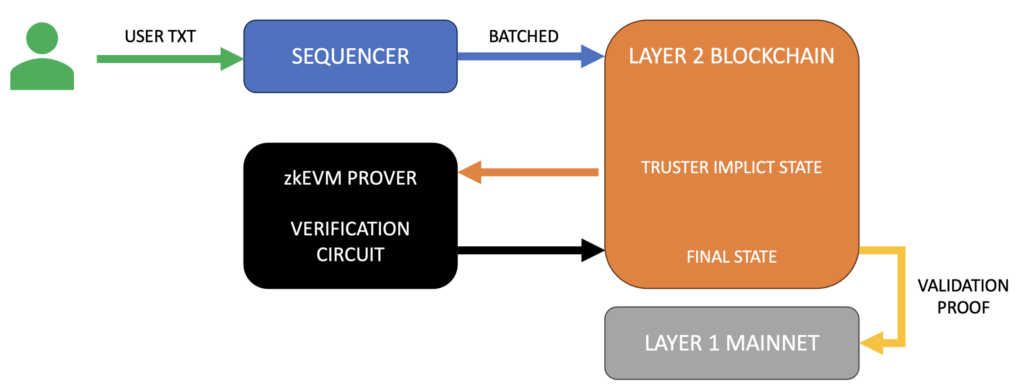
- User transactions (user TXs):
The process begins with users initiating transactions on the Layer 2 network. These transactions could be token transfers, smart contract interactions, or any other operations supported by the underlying blockchain. - Sequencer:
The Sequencer is a critical component that collects and orders user transactions. Its primary function is to batch these transactions, optimizing them for efficient processing and verification. This batching reduces the computational load on the system and improves overall throughput. - Layer 2 blockchain:
The batched transactions are then sent to the Layer 2 blockchain. This L2 chain maintains two key states:- Trusted Implicit State: This represents the current state of the L2 blockchain before processing the new batch of transactions.
- Final State: This is the resulting state after applying the batched transactions.
- zkEVM prover and verification vircuit:
This is the core of the Zero Knowledge system. The zkEVM (Zero Knowledge Ethereum Virtual Machine) Prover takes the batched transactions and the state transition (from Trusted Implicit State to Final State) as inputs. It then generates a cryptographic proof, often referred to as a Validity Proof, that attests to the correctness of this state transition.
The Verification Circuit is a predefined set of constraints that the proof must satisfy. It encapsulates the rules of the blockchain, ensuring that all state transitions are valid according to the protocol’s rules.
- Validity proof:
The Validity Proof is a succinct cryptographic proof that demonstrates the correctness of the state transition without revealing any specific details about the transactions themselves. This proof has two key properties:- Zero Knowledge: it proves the validity of the transactions without revealing any information about the transactions themselves.
- Succinctness: the proof is small and quick to verify, regardless of the complexity of the computations it represents.
Advanced zk-SNARK systems often employ recursive proof composition, where multiple proofs are aggregated into a single, verifiable proof. This technique allows for the creation of “proofs of proofs,” enabling the verification of complex computations through a series of smaller, more manageable proofs.
- Layer 1 mainnet:
The Validity Proof is then submitted to the Layer 1 blockchain (e.g., Ethereum mainnet). The L1 smart contract verifies this proof, and if valid, updates its records of the L2 state.
This zero-knowledge architecture provides a powerful framework for scaling blockchain transactions while maintaining security and privacy. By leveraging cryptographic techniques such as polynomial commitments, elliptic curve pairings, and proof composition, zk-proofs enable the verification of complex computations with minimal on-chain footprint.
The list of solutions using this kind of architecture is numerous:
- zkSync (by Matter Labs):
- Uses this type of architecture for their zkEVM
- Employs PLONK for their zkSNARK construction
- Utilizes a custom-built zkEVM for Ethereum compatibility
- Polygon zkEVM:
- Follows a similar structure in their zero-knowledge rollup solution
- Uses a custom zkEVM prover based on the Groth16 proving system
- StarkNet (by StarkWare):
- Hermez Network (now part of Polygon):
- Loopring:
- Implements a comparable process for their zkRollup DEX and payment protocol
- Uses the ethsnarks library for zero-knowledge proofs
- Aztec Connect:
- While focused on private transactions, it uses a similar architecture for its zk-rollup
- Employs their own zkEVM called Noir
- ZKSpace (previously ZKSwap):
- Uses a comparable structure for their Layer 2 DEX and payment platform
- Utilizes the ZoKrates toolbox for their zero-knowledge proof system
Having explored the foundations of Zero Knowledge proofs, let’s turn our attention to Zk-rollups, a pivotal evolution in this technology.
ZK-rollups: scalability & efficiency
Before delving into ZK-Rollups, it’s crucial to understand ZK-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge), the cryptographic backbone of this technology. ZK-SNARKs represent a significant advancement in Zero Knowledge proofs, offering a powerful combination of privacy, efficiency, and scalability.
The term “Succinct” in ZK-SNARKs refers to the proof’s small size and quick verification time, crucial for blockchain applications where efficiency is paramount. “Non-interactive” means that the prover and verifier don’t need to communicate back and forth; a single proof is sufficient. “Arguments of Knowledge” implies that the prover demonstrates knowledge of certain information, rather than just the truth of a statement.
ZK-SNARKs allow for the verification of computations without revealing the inputs or intermediate steps. This property makes them ideal for blockchain applications, where transparency and privacy often need to coexist. In the context of Ethereum and other smart contract platforms, ZK-SNARKs enable the compression of complex computations into compact, easily verifiable proofs.
ZK-Rollups apply ZK-SNARK technology to Ethereum, with enormous potential benefits given the network’s congestion. It’s predicted that these Zero Knowledge-based second-layer rollups could scale Ethereum by orders of magnitude. While some conservative estimates suggest a 100-fold increase to about 2000 transactions per second, more optimistic projections indicate the potential for tens of thousands of transactions per second. However, it’s important to note that exact numbers can vary based on implementation and are often theoretical maximums.
Beyond providing scalability, ZK-Rollups also enable new use cases with a higher level of privacy. For example, in a recent paper, Vitalik Buterin proposed a system called “Privacy Pools” that leverages ZK-SNARKs to balance privacy needs and regulatory compliance in financial transactions.
Users can prove that their funds do not come from illicit sources while remaining anonymous. This way, authorities can identify illegal capital, while users maintain a certain degree of confidentiality. This concept aims to address the “tainted coins” problem in cryptocurrency, where funds can be traced back to illicit sources.
According to Buterin, this approach could enable private but legal financial services even in the traditional banking system. ZK proofs thus offer interesting possibilities for regulated innovation.
A possible balance between technology and regulation?
More generally, the relationship between blockchain and privacy regulations remains an open challenge. The technology aims for transparency, often in contrast with laws like GDPR. However, it’s worth noting that this is mainly an issue for public blockchains. Private or permissioned blockchains can be designed to be GDPR-compliant more easily. At the same time, tools like Zero Knowledge provide ways to ensure confidentiality on a public and immutable ledger.
The implications extend beyond cryptocurrencies. As Buterin suggests, this approach could enable private yet legal financial services even within the traditional banking system. ZK proofs thus offer a pathway for regulated innovation, potentially revolutionizing how we think about privacy and compliance in digital finance.
Regulators are still in the process of evaluating how to apply existing frameworks to cryptocurrencies and decentralized systems. Some jurisdictions, like the EU with its Markets in Crypto-Assets (MiCA) regulation, are working on crypto-specific rules. The challenge lies in finding the right balance between transparency, privacy, and regulatory oversight.
Zero Knowledge proofs, with their ability to provide verifiable privacy, may well be the key to unlocking this potential. By enabling systems that are both private and auditable, they could pave the way for a new era of digital finance that respects user privacy while meeting regulatory requirements.
Joint efforts between developers, communities, and institutions will likely be needed to produce a tailored model for the crypto world. Blockchain technology and regulation will need to work in symbiosis to enable solutions that reflect decentralized values and protect user privacy. And, maybe, Zero Knowledge could be an answer.
For further inquiries or assistance with Blockchain integration, Ethereum, Bitcoin or digital assets, feel free to reach out.
Notes and further reading
For those interested in delving deeper into L2 and ZeroKnowledge, here are some valuable resources and recent articles:
Layer 2 solutions:
- “Scaling Ethereum for mass adoption” – Official Ethereum documentation on L2 solutions
- “An Incomplete Guide to Rollups” by Vitalik Buterin
ZeroKnowledge proofs (ZKPs):
- “Introduction to Zero-Knowledge Proofs” by Ethereum Foundation
- “ZK-SNARKs and ZK-STARKs Explained” by Binance Academy
ZK rollups:
- “ZK Rollup Zero Knowledge” by Ethereum community
- “Polygon zkEVM” – Official documentation by Polygon
Optimistic rollups:
- “All about optimistic rollups and Arbitrum” by Pontem Network
Privacy in blockchain:
- “Privacy on the Blockchain” by Vitalik Buterin
Technical deep dives:
- “Ground Up Guide: zkEVM, EVM Compatibility & Rollups” by Immutable
- “Learn ZCASH” by Zcash Foundation
Industry report:
- “The State of ZK” by Mina Protocol
